Significant Data Breaches and Cyber Attacks Discovered or Reported in 2020
The following are some of the cyber-attacks, breaches, malicious campaigns from the year 2020, that I came across and found significant and/or interesting. You will notice that the 6 attacks listed below are all different, with some of the techniques overlapping, while others unique to the specific attack. Types of attacks listed below are DDoS, Social Engineering, Malware, Credential Stuffing and Supply Chain attacks. The list should not be considered exhaustive.
THE LARGEST DDOS ATTACK RECORDED BY BANDWIDTH IN 2020
Amazon uses AWS Shield to protect its customers from all kinds of layer 3 to layer 7 DDoS attacks. In early 2020 it thwarted the largest ever DDoS attack seen by AWS Shield.
Attack Vector
This was a single vector attack, using CLDAP reflection method. This attack works on UDP connectionless protocol and therefore has a greater potential for amplification.
Such types of attack can be prevented by disabling UDP port for LDAP service on the firewall and/or creating an exception in the firewall for the application that needs to use LDAP over UDP.
You can read more about the attack here.
A MALWARE ATTACK WHICH SPIED ON GOOGLE CHROME USERS THROUGH 33 MILLION DOWNLOADS OF MALICIOUS CHROME EXTENSIONS
An everyday user performs most of his/her activities on the browser, such as Microsoft Edge, Google Chrome, Apple’s Safari etc. It can be troubling to find out that the very browser that you are using to check your bank account, send email or book travels etc. is spying on you. Chrome users might have unwittingly given away sensitive information, if they were the victim of this attack.
The attack uncovered by Awake Security made use of fake Google Chrome extensions, downloaded directly from the Chrome Web Store and other websites.
These extensions were advertised to perform useful functions such as securing your browser or converting files into different formats.
However, in reality these extensions once installed, would steal sensitive user data. The information would then be uploaded to malicious domains, roughly over 15,000 in number as uncovered by Awake Security.
As you can see, it’s hard to distinguish genuine extensions from fake ones.
HOW DID THESE FAKE EXTENSIONS AVOID DETECTION?
Well, first of all these extensions should not have been on the official Google chrome web store in the first place. The fact that they were there, means Google automated and manual vetting process failed. Google removed them as soon as they found out about this.
The malicious extensions behaved differently from network to network. The extension would direct the user to a malicious page and exploit, if the network did not have any threat detection tools. On the other hand, the extension would direct the user to a benign landing page, if it was on a network with scanning and threat detection tools. In other words, a normal user was more than likely to be exploited if they had these extensions installed.
In some cases, the malicious domains would allow requests originating only from the malicious extension installed on the user’s browser. This means any request coming from any threat analysis tool would be rejected, potentially avoiding detection.
LESSONS:
Do your research before installing any browser extensions.
Spend some time in reading reviews and reading about the developer.
Make sure that your default browser is genuine and does not come with preinstalled extensions that you don’t want.
It’s a good idea to check what extensions you have currently installed. Remove them if you don’t need them.
You can read the detailed report from Awake Security here.
A SOLARWINDS SUPPLY CHAIN ATTACK WITH A MASSIVE BLAST RADIUS - ALSO KNOWN AS SUNBURST OR SOLORIGATE
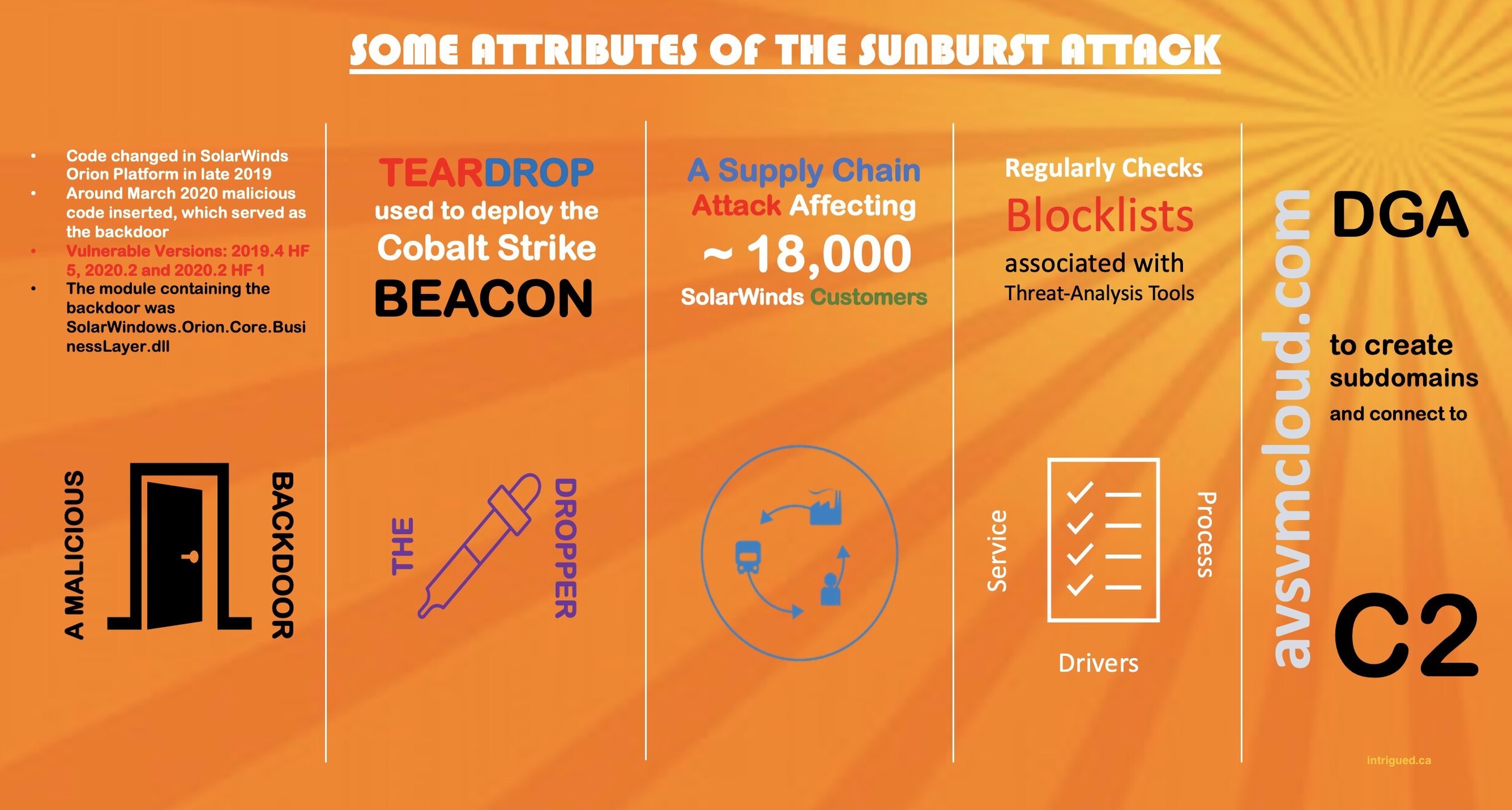
This attack can easily be categorized as one of the biggest and most sophisticated attack of 2020. Microsoft tracks it as Solarigate and FireEye as Sunburst.
BACKGROUND:
SolarWinds make different IT/Network products, which are in demand with government as well as private organizations, including fortune 100 companies.
Malicious code was inserted into the SolarWinds Orion suite of products in early spring 2020, which served as the backdoor. This might have been made possible by compromising the internal build distribution environment of SolarWinds.
Orion Suite of products offers very useful feature for large enterprises. Features range from comprehensive network monitoring, configuration deployment and management, log analysis, alerting, performance analysis and much more. Needless to say that these tools are an integral part of any successful enterprise deployment.
This backdoor in Orion remained hidden until December 2020, when FireEye started to investigate breach of their Red Team tools. The investigation lead to compromised machines running Orion software.
Microsoft and FireEye reverse engineered the code and gradually started to unravel the working of the malicious code.
By then more than 18000 SolarWinds customers would have downloaded the trojanized version of the Orion software.
This means the malicious code could potentially be running in the networks of the organizations, which installed the trojanized Orion suite of products.
Sunburst Attack Victims by Sector
KEY THINGS ABOUT THE ATTACK:
Digital certificates used for signing the software were compromised. This means that even a compromised software would appear legitimate since it was signed by a valid Code Signing certificate.
Teardrop malware was used to deploy BEACON. Beacon can perform a variety of of functions such as key logging, command execution, file transfer, lateral movement etc.
Sunburst does not work if the system is not domain joined. This is intentional to avoid detection.
The Sunburst malware had its own blocklists, which it would consult from time to time to avoid detection. The blocklists contained processes, services and drivers for the anti-virus and threat analysis tools. In other words, it does not execute if it thinks that there is a possibility of detection.
Sunburst checks when the last time the Orion software ran and executes only 12 days plus some random time after that. This random execution was one of the techniques to avoid detection.
Sunburst made use of DGA (Domain Generated Algorithm) to generate the subdomains. Another evasive technique.
The malware communicates over HTTP, once DNS resolution is completed successfully.
Possible Victims of the Trojanized Orion Software
Although the attacker was able to access the internal networks of different organizations, it is not clear yet how if any confidential data was exfiltrated. We know that FireEye’s Red Team tools were stolen. We might come across some more information regarding what was stolen in the future.
SolarWinds has issued an update of its Orion software, which will get rid of the backdoor. But sophisticated nature of the attack means, that forensic analysis of the infected networks would still be required, which can be a long and arduous process. You can read about the attack in greater detail here and here.
A HIGH-PROFILE SOCIAL ENGINEERING SPEAR PHISHING ATTACK TARGETED TOWARDS TWITTER
This attack did not hack huge number of twitter users. In fact, there were only 130 accounts that were hacked, out of which data was downloaded from only 7 accounts. The reason this hack is significant is because it targeted high profile users, such as Barak Obama, Elon Musk etc.
According to Twitter, its employees became victim of a phone spear phishing campaign. This gave hackers access to information regarding some Twitter’s internal processes. The information wasn't enough to hack high profile accounts, but it was enough to target other Twitter employees, who might have had access to Twitter’s internal support tools. Once the attackers hacked those employees, they were able to target high profile Twitter accounts.
There were a few individuals arrested as a result of this hack. Twitter promised to make its systems more secure, which are known to be less secure. You can read more here.
SPOTIFY CREDENTIAL STUFFING ATTACK AGAINST ROUGHLY 300,000 USERS
VpnMentor discovered a database hosted on an unsecured server on the internet. This database contained 380 million records. Roughly 300,000 of these records were account details of Spotify users.
Exposed Data
These stolen account details which contained login credentials and email addresses were used to launch a credential stuffing attack against applications for an unauthorized access or to launch other phishing and identify theft attacks.
Spotify initiated a rolling reset of the passwords for the affected users as a result of this attack.
AN IPHONE-IOS ZERO-CLICK, ZERO-DAY HACK OF AL-JAZEERA’S JOURNALISTS
This attack involved hacking Al-Jazeera’s journalists’ phones. The attack was made possible by exploiting a zero-day vulnerability on Apple’s iOS 13 software. Citizenlab, who investigated the attack called this zero-day exploit Kismet.
The attackers were able to install Pegasus spyware on the iPhones with the help of this Kismet exploit, which was also zero-click in nature (no user intervention was needed).
As detailed in citizenlab’s thorough research piece, the initial vector of attack was Apple servers, enabling Zero-click attack through either iMessage or FaceTime app. Zero-click nature of attack meant that the iPhone user didn’t have to click on any link or perform any task, other than regular use of the app, on his/her iPhone for the attack to be successful.
Kismet Zero-day vulnerability was fixed in iOS14. Apple further enhanced the security of its iMessage app last month by introducing BlastDoor service for iMessage, which basically makes the app tightly sandboxed unlike in iOS13.
By learning about these attacks, we can adopt many best practices at an enterprise and individual level. This may include use of multi-factor authentication, monitoring outbound and inbound traffic flows, revisiting C2 domains, disabling things which are not really required such as disabling macros, monitoring logging patterns, only using the extensions which are thoroughly vetted and have genuine reviews etc. I hope you enjoyed reading this article as much as I enjoyed writing it. Until next time.